Enabling Kerberos in Firefox for all users
2015-10-16
Table of Contents
Abstract
Users can enable Kerberos single sign-on (SSO) authentication using preference in their browser profile but it's also possible to set the default for all Firefox users on the system.
User settings in about:config
Firefox users may change the preferences of their profiles using → , which in latest Firefox versions actually leads to about:preferences page. However, preferences related to the Negotiate HTTP authentication which is the mechanism used for GSS-API and Kerberos authentication are not here but in about:config page which lists all options in tabular form.
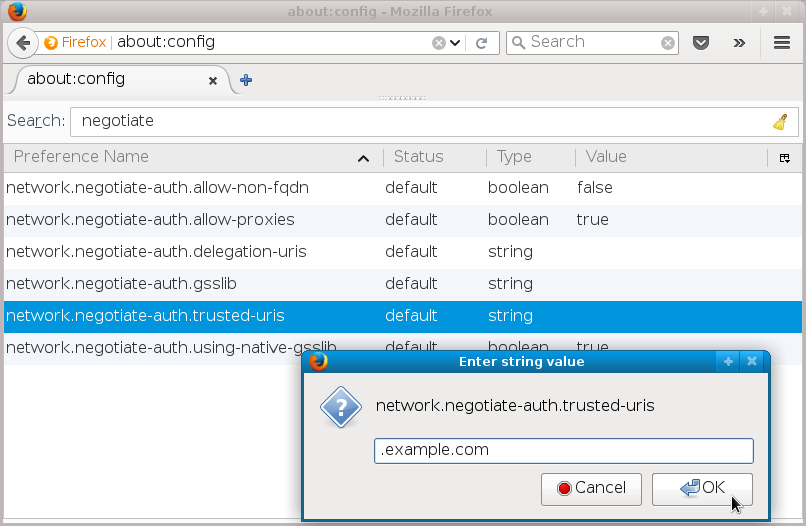
The option we are looking for is network.negotiate-auth.trusted-uris.
Users can set it to contain comma-separated list of domains
or URL prefixes for which the Negotiate HTTP authentication
should be attempted.
1: Modifying trusted-uris value
2: The trusted-uris was set by user
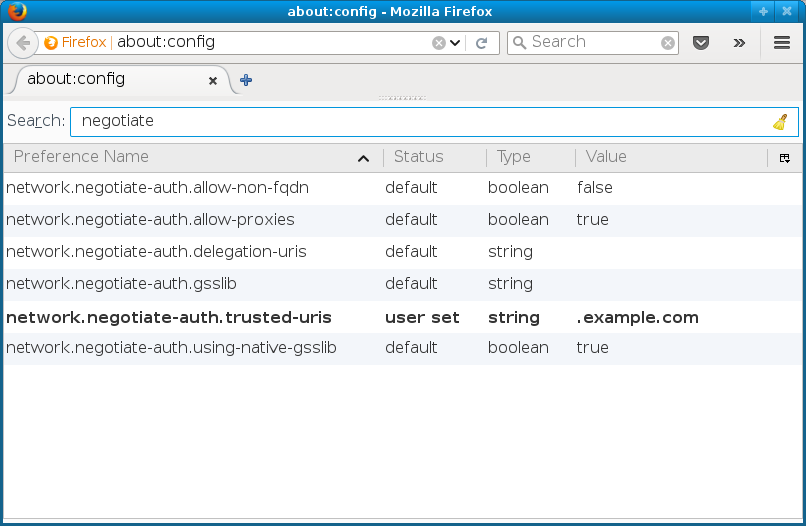
For Kerberos it means that when accessing site matching
the domain or URL and if the request is met with HTTP status
401 Unauthorized and HTTP response header
WWW-Authenticate: Negotiate, the browser will
check the Kerberos ticket cache and if it finds ticket-granting
ticket for realm corresponding to the domain (check
/etc/krb5.conf), it will attempt to get service
ticket for HTTP/ service. It then retries the
request with the GSS-API data containing the service ticket,
which the server verifies and authenticates the user. Or in
simpler terms, the browser will use Kerberos authentication
against servers that support it and that match the domain
or URL prefix in the network.negotiate-auth.trusted-uris list, for example www.example.com.
Changing the defaults
When Firefox is started, it reads global preferences files from
/usr/lib64/firefox/browser/defaults/preferences/ directory (on 32-bit systems, use /usr/lib/...). To change the default for all users that will
run Firefox on that system, run
# echo 'pref("network.negotiate-auth.trusted-uris", ".example.com");' > /usr/lib64/firefox/browser/defaults/preferences/kerberos.js
or use some other mechanism to put line
pref("network.negotiate-auth.trusted-uris", ".example.com");
in some .js file in
that directory. Configuration management will work and so will
distributing that file packaged in rpm — check
a .spec file
which can be used to build configuration rpm for your organization.
3: Modified default value
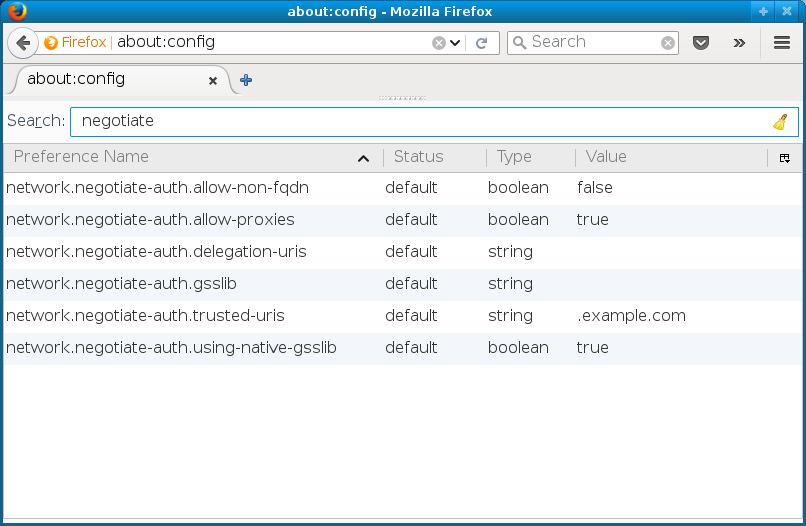
Note that the value .example.com is now
marked as default. The user can still modify the value in their
profile, to perhaps add additional domains, but if they
the value (right click on
the line brings the menu), it will revert to this default
value.
Configuring with ipa-client-install
In setups when the machine is being IPA-enrolled using
ipa-client-install, it is possible to let
it also configure the Firefox defaults using the mechanism described
above. The option is called --configure-firefox
and typical process would be:
-
Create the host record on IPA server, generate one-time password:
ipa$ ipa host-add --random client1.example.com -------------------------------- Added host "client1.example.com" -------------------------------- Host name: client1.example.com Random password: A5dGy0WlXK5E Password: True Keytab: False Managed by: client1.example.com
-
On the machine which is being enrolled, use that
one-time password plus the option to configure Firefox:
client1# ipa-client-install -w A5dGy0WlXK5E --configure-firefox -U [...] Firefox sucessfully configured. [...] Client configuration complete.
In Firefox default preference directory, file
all-ipa.js will be created with the
IPA domain configured as the trusted URI:
/* Kerberos SSO configuration */
pref("network.negotiate-auth.trusted-uris", ".example.com");
There are also additional network.negotiate-auth.*
value configured in that file but they just repeat the
defaults that are already there on latest Firefox versions.